Gatehouse Cyber Blog
Analysis for Humans: Inbox Rules
Approaches and Methodology for reviewing User Inbox Rules, for those who refuse to automate
Relevant operations: New-InboxRule, Set-InboxRule, Enable-InboxRule, Set-Mailbox, Enable-TransportRule, New-TransportRule, Set-TransportRule
BEC Incident Lifecycle: Persistence, Evasion, Exfiltration

The Basics
Inbox Rules are a feature that allow users to set up rules that automatically take actions on specific emails, typically to organize emails into folders by sender or subject, or to respond to emails, such as an out of office response.
The Inbox Rule feature also has the dubious honor of near ubiquitous malicious use in Business Email Compromise incidents. Threat Actors use Inbox Rules to hide incoming emails from the legitimate mailbox owner or exfiltrate data by automatically forwarding emails externally.
The effects of an Inbox Rule continue until the rule is deleted. Some impacted organizations find that their users are affected by malicious Inbox Rules from unremediated incidents from years prior.
In all incidents, Gatehouse Cyber automates review of every Inbox Rule and related event across the client tenant.
In a recent incident, we found that the client had been impacted by a prior compromise one year before our investigation, and the CEO was still affected by an Inbox Rule that hid emails from one of their banks.
Our Analysis Procedure:
Despite the potential impact, the majority of Inbox Rules we review are legitimate. Below are some of the principles that underly our procedures and detection methodology for reviewing Inbox Rules:
Event data:
Before getting into the actual content of the event, we look at the same components we use when reviewing all events: IP Address/ISP/Country, User, Timestamp, usage of Indicators of Compromise, etc.
For example:
- If we see that an Inbox Rule was created 3 months before the phishing email that initiated the incident, we can increase the confidence level that the rule is unrelated to the current incident, although that does not make the rule legitimate.
- If a user uses an IP address that they have used for the past two years to create the rule, it is more likely that the rule is legitimate. On the other hand, if a known Indicator of Compromise is used to create the rule, then it is likely malicious.
- Caveats: This does not address insider risk concerns, and some clever Threat Actors use VPNs or proxies from legitimate sources (Verizon, AT&T, Comcast, etc.).
Inbox Rule Contents:
There are some detection procedures we can follow in reviewing the content of Inbox Rules too. Common sense goes far here too.
Inbox Rules define a subset of affected emails and specify an action to be taken.
Rules that target sensitive organizations, like banks, or certain vendors are higher risk. Rules that target broader sets of emails, such as all emails received from a web domain, or with a certain substring in the subject line (say "finance" or "payment") also tend to be riskier than rules that affect individual senders or very specific subject lines.
The main risks inherent to Inbox Rules are that important or fraudulent emails will be hidden from the user, or that sensitive data will be exfiltrated by the threat actor (by being sent externally).
Rules that mark emails as read, delete emails, or move emails to folders that no one ever checks, such as RSS Feeds, Archive, or Conversation History, are higher risk.
A rule that moves emails to a specific folder that does not look like an attempt to hide those emails is less likely malicious. For instance, moving emails from jim@vendor.com to a folder called "Vendor communications" is less likely to be malicious.
Threat Actors tend to give extremely brief or easily overlooked rule names or names that contain random characters. Rule names that contain only punctuation or are a few random letters are quite common and almost always malicious.
In the wild:
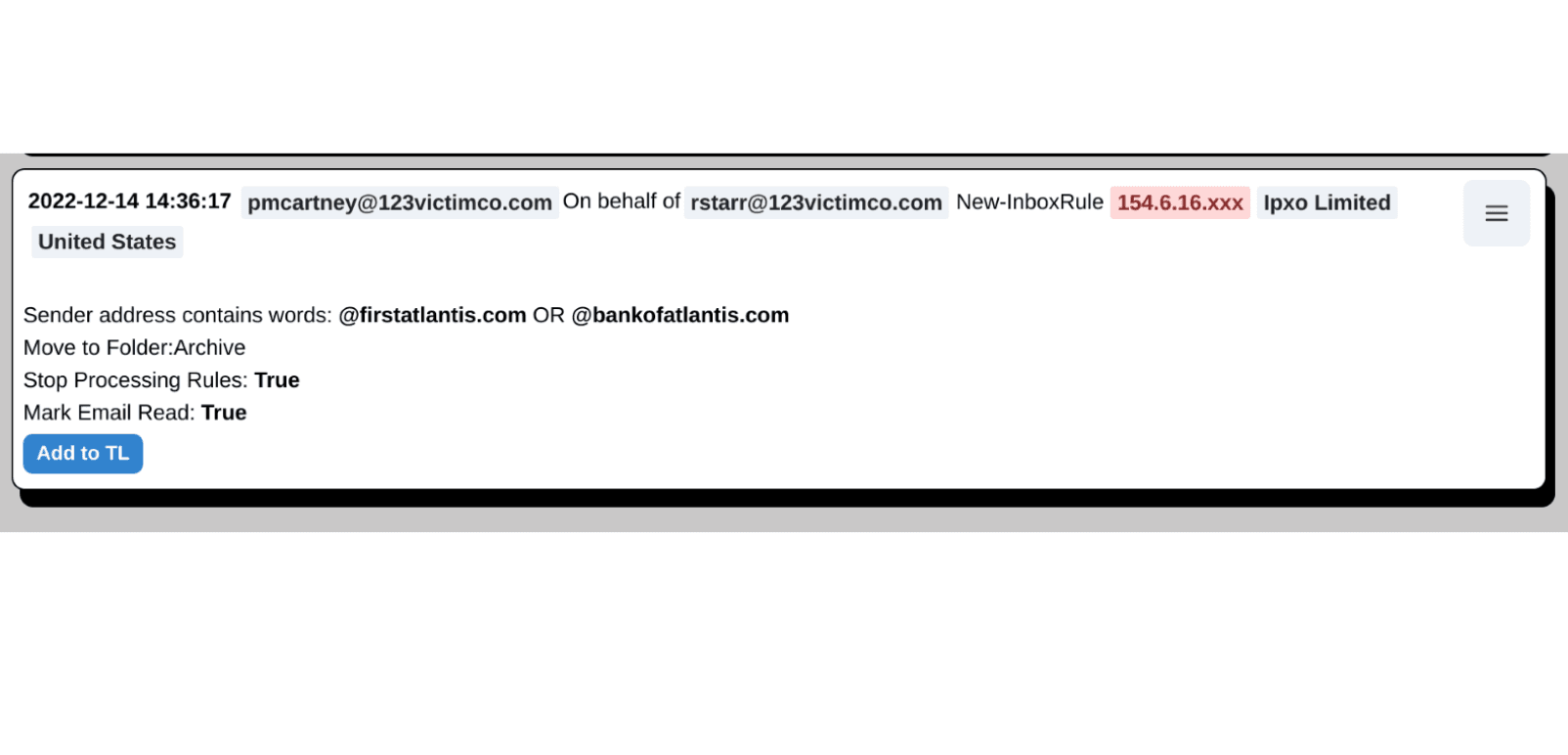
Below is an example Inbox Rule reviewed by Gatehouse Cyber for a client in a recent incident. See for yourself, what detections you find on this Inbox Rule, vs. the automated detections flagged in our analysis.
Experiencing an Active Incident?
Want to be prepared before an incident can occur?
Contact
+1 (240) 994-0568
2024 Gatehouse Cyber LLC. All rights reserved.